Low Cost SimpliSafe Attacks
Earlier this week, Dr. Andrew Zonenberg of IOActive published a security advisory and blog post describing weaknesses in the SimpliSafe home security system. He showed that components of the system, such as the keypad, transmit unencrypted radio signals that can be captured and replayed. He also pointed out the significant problem that SimpliSafe devices are physically incapable of being reprogrammed with improved firmware that might address such vulnerabilities.
I know Andrew and have great respect for his reverse engineering and hardware hacking talents. He implemented a replay attack by making small modifications to SimpliSafe devices, monitoring and controlling them from his own hardware platform. To demonstrate the impact of the technique, he showed how it could be used to replay a PIN that disarms a SimpliSafe system. While I found his attack very effective, I was intrigued by his inability to fully decode PINs. I wanted to take a crack at the problem myself, and I thought it would be worthwhile to confirm that the radio interface of the system can be attacked at a lower cost to the attacker, without any SimpliSafe hardware, and without physical proximity to the target system.
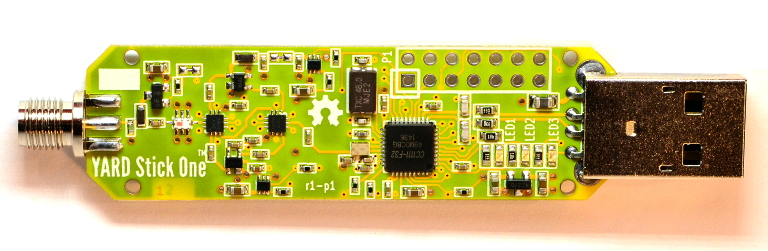
I borrowed a SimpliSafe system to use as a target system, and I took the approach I have demonstrated in my presentation, Rapid Radio Reversing, using a combination of Software Defined Radio (SDR) and non-SDR tools. The primary tool I used was YARD Stick One with RfCat software.

First I used HackRF One to monitor transmissions from the SimpliSafe keypad. I visualized a captured radio waveform with inspectrum and quickly identified an Amplitude Shift Keying (ASK) signal being transmitted by keypad. Andrew labeled this On-Off Keying (OOK), but the difference between ASK and OOK is subtle and does not affect his findings.
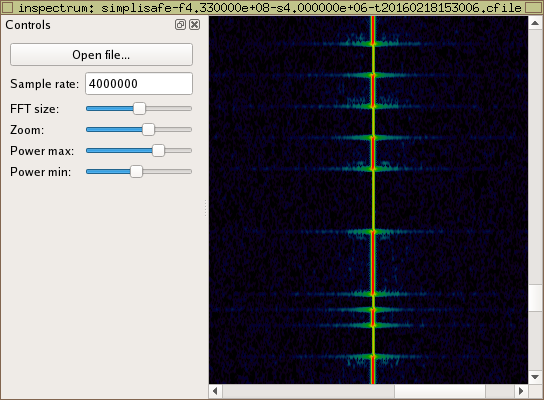
After determining the frequency, modulation, and symbol rate of the transmission, I turned to YARD Stick One for further analysis. Within seconds I was able to decode raw symbols being transmitted by the keypad. It was easy to identify which packets were transmitted by the keypad after entering a PIN, so I entered a few different PINs and saved the resulting packets for analysis.
It took me a couple hours of staring at packets and fiddling with short decoding functions in Python before I was able to understand the encoding. This was the most difficult part of the project. The system uses a somewhat uncommon Pulse Interval and Width Modulation (PIWM) to encode data onto the ASK signal, and the order of bits was not immediately obvious. With a little time, however, I was able to implement real-time decoding of received packets and to recover the PIN entered on the keypad by another person at a distance. I was also able to replay keypad transmissions.

I could have implemented capture and replay even without fully decoding the packets. This is what Andrew was able to accomplish with his hardware hack. Full decoding, however, demonstrates that some additional attacks are possible. An attacker with a good antenna can monitor PINs from a great distance and can, without ever transmitting a radio signal, learn those PINs and later use them at the keypads. An attacker can craft packets with chosen PINs or other contents, so an automated brute force attack on a PIN is possible even if the attacker has not observed the valid PIN. The system uses 4-digit pins, so only 10,000 guesses are required for an exhaustive brute force attack.
I could have accomplished all of this with only HackRF One or only YARD Stick One, but I used the combination of the two for convenience. If I had to choose just one for a project like this, it would be YARD Stick One which, at $100, costs less than half of the equipment used by Andrew. It could be done with almost any 433 MHz ASK transceiver, including the covert TURNIPSCHOOL or my favorite children's toy, the IM-Me, but YARD Stick One with RfCat is the most convenient tool for the job in my toolbox.
Andrew included with his blog post a video demonstrating his attack over-the-air. In his video, he mentions that his hardware hack was the "quickest and easiest way" to accomplish his attack. That may be true for Andrew, but personally I found it easier to use radio tools. I wrote dozens of lines of Python compared to his hundreds of lines of C, and I never needed to crack open any SimpliSafe device. It took me about half a day, and most of that time was spent puzzling over the data encoding. I could have implemented a simple capture and replay within seconds of identifying the radio signal.
Andrew's video shows him disarming an alarm from only a few inches away which unfortunately could be interpreted as meaning that his attack is only effective at such close range. His attack, in fact, works from anywhere the keypad can operate. According to the manual, it works within 100 feet of the base station. Even greater range can be achieved easily with the use of low cost radio test tools instead of a modified keypad. I estimate that, for less than the $250 Andrew spent, an attacker can execute PIN replay from about a mile away.
Since Andrew's advisory, SimpliSafe has responded in predictable fashion while information security professionals filled their bingo cards. One of the things SimpliSafe has pointed out is that customers are notified whenever their systems are disarmed. Unfortunately this is only true for those customers who pay an extra $10 per month for SMS and email notifications. Moreover, in my testing, I verified that it is possible for an attacker to wirelessly command the SimpliSafe system to enter test mode even while the system is armed. This is something that normally can be done from the SimpliSafe keypad only while the system is disarmed. Alarms and notifications are disabled in test mode, but the documentation states that test mode is indicated in the online dashboard available to customers who pay for notifications.
Following Andrew's lead, I am not publishing any attack software developed during my testing. However, it is important to realize that I employed only tools and techniques that are well known and commonly used throughout the wireless security community. Effective attacks, including PIN replay, can be implemented without writing a single line of code. Passive monitoring attacks, such as the ability to learn a PIN at a distance, require somewhat more reverse engineering effort but can be implemented with even less expensive equipment such as off-the-shelf TV tuners that cost as little as $10.
Andrew's and my investigations only scratch the surface of the security of the SimpliSafe system. Andrew's key finding is not that PINs can be replayed but that the absence of basic cryptographic protections illustrates a total lack of wireless security engineering. Further weaknesses will very likely be discovered if anyone takes the time to look for them. For example, the cellular interface is an attack vector that remains unexplored as far as I know.
SimpliSafe is not alone in deploying alarm systems with vulnerable wireless interfaces. Sadly, almost every wireless alarm system I've ever looked at suffers from similar weaknesses. As we hurtle toward a future of ubiquitous digital wireless technology embedded in the objects of our daily lives, we would be wise to pay more attention to the security of those wireless interfaces. Burglar alarm systems seem like a good place to start.
P.S. Dr. Zonenberg's dissertation is fascinating.